
A Trojan-style malware that did the rounds a couple of years ago has risen from the ashes, and is reportedly going after Israeli fintech and cryptocurrency trading software companies.
The Cardinal RAT malware was first spotted back in 2017 and went largely undetected for two years. It used a novel technique to infect computers, using a downloader called Carp and malicious macros in Microsoft Excel documents to compile the source code into an executable which then deploys the malware.
However, the malware is resurfacing after a recent series of updates which help it “evade detection and hinder analysis,” according to researchers from Palo Alto Networks’ Unit 42.
The latest incarnation of Cardinal RAT implements a number of techniques to make analyzing attacks more difficult, one of which is steganography. While it sounds complicated, steganography refers to a group of programming techniques that are used to obscure files, messages, and other data.
The Cardinal RAT malware uses data embedded into a Bitmap (BMP) image file that is loaded on to the victim’s computer during installation. On the surface it looks like a harmless logo, but when the image is opened, the malicious code embedded within it is decoded and executed initiating the attack.
During the attack, the malware will attempt to steal passwords, usernames, and other sensitive data. It then sends all this back to the malware operators, potentially giving attackers the power to steal victims’ cryptocurrency. It can also take screenshots of the victim’s machine.
Unit 42 identifies the following actions in Cardinal:
- Collect victim information
- Update settings
- Act as a reverse proxy
- Execute command
- Uninstall itself
- Recover passwords
- Download and Execute new files
- Keylogging
- Capture screenshots
- Update Cardinal RAT
- Clean cookies from browsers
Since 2017, only two Cardinal RAT attacks have been observed. According to Unit 42, both victims were fintech companies based in Israel that make software for forex and cryptocurrency trading. The exact details of the companies have not been disclosed. Hard Fork has contacted Unit 42 for further clarification on how the companies were affected.
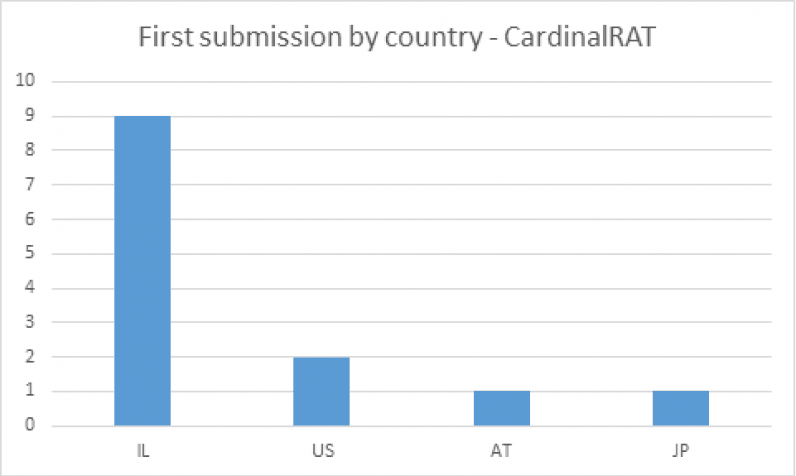
Indeed, Israel seems to be the malware’s main target. There have been a total of nine reports of this malware from Israel, two from the US, and one each from Austria and Japan.
Unit 42 believes that the malicious files find their way onto machines through lure documents attached to spam messages that were sent to individuals thought to operate as forex and cryptocurrency traders.
With that in mind, if you have effective spam filters, and properly maintain your systems, you are at a much lower risk of infection. Unit 42 also recommends that you don’t accept e-mails from external sources where attachments contain macros.
Want to find out more about cryptocurrencies and blockchain technology? Check out our Hard Fork track at TNW 2019!
Get the TNW newsletter
Get the most important tech news in your inbox each week.




