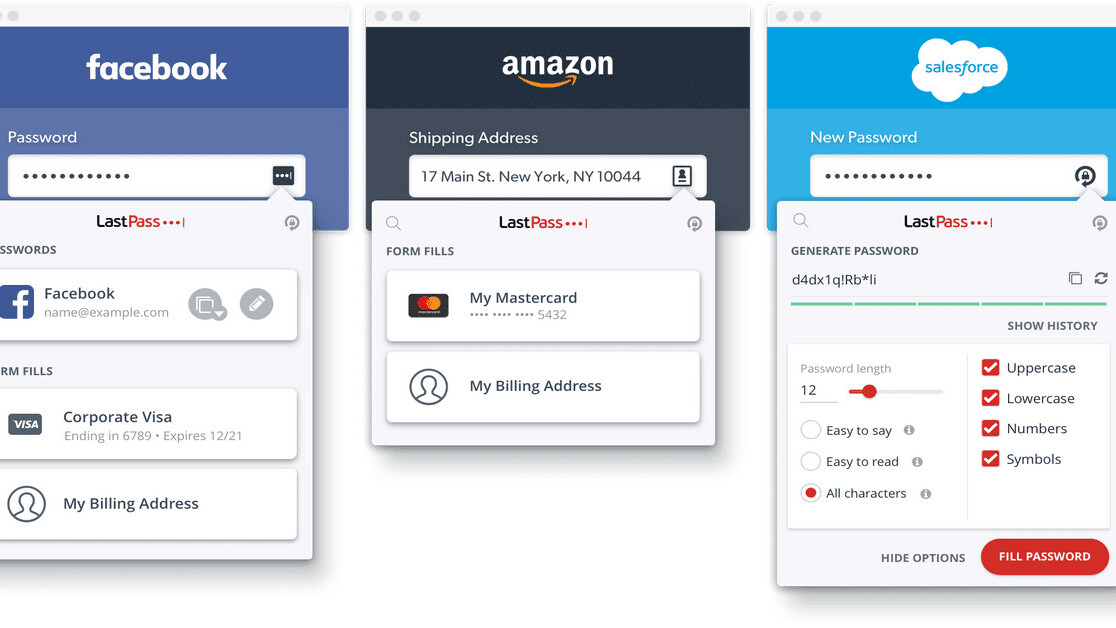
Popular password manager LastPass has fixed a serious flaw in its latest update that potentially allowed a malicious website to access the last used credentials entered by the browser extension.
The clickjacking bug was discovered on August 30 by Google Project Zero researcher Tavis Ormandy, who is part of the white-hat hacker group devoted to finding bugs in software. But there’s no evidence that the flaw was exploited to steal credentials in this way.
Clickjacking is what happens when a user is tricked into clicking something malicious that’s layered on top of a visible link that’s deemed innocuous, thus accidentally revealing confidential information, or even letting threat actors remotely take control of a system.
“To exploit this bug, a series of actions would need to be taken by a LastPass user including filling a password with the LastPass icon, then visiting a compromised or malicious site and finally being tricked into clicking on the page several times,” LastPass acknowledged in a statement.
Noting that the issue was specific to Chrome and Opera, LastPass said it has deployed an update to all browsers out of precaution. The extension for Chrome and Opera should have the version 4.33.0, while the Firefox variant should be 4.33.4.2.
LastPass could leak the last used credentials due to a cache not being updated. This was because you can bypass the tab credential cache being populated by including the login form in an unexpected way! https://t.co/bfLdDzSWS5
— Tavis Ormandy (@taviso) September 16, 2019
The details of the flaw — which have now been made public — reveals that it stems from the way the extension generated popup windows to autofill passwords.
A malicious website could, therefore, produce a popup by executing simply a piece of JavaScript code to pull credentials, and worse, mask its intent behind a Google Translate URL. An attacker could then trick users into visiting the link, and subsequently extract credentials from a previously visited site in the same tab.
Although Ormandy labeled the bug as high severity, LastPass has tried to minimize its scope, stating the flaw “revealed a limited set of circumstances on specific browser extensions that could potentially allow an attacker to create a clickjacking scenario.”
Just because LastPass had a security scare doesn’t mean you should give up on password managers altogether.
In reality, they are a much more secure alternative to storing passwords in the browser, from where they can be easily accessed by threat actors. However, bear in mind that not all password managers are created equal.
Ultimately, whether you’re using LastPass or otherwise, the same rule of security hygiene applies: use two-factor authentication to secure your accounts (including password managers), set a unique password for each account, and never reuse your old passwords.
Get the TNW newsletter
Get the most important tech news in your inbox each week.