An unsecured server of the Indian ticket platform RailYatri exposed the personal information of over 700,000 passengers. The details in the database included full names, phone numbers, addresses, email IDs, ticket booking details, and partial credit or debit card numbers.
The Indian railway network is one of the busiest transportation systems around the world, catering to over 24 million passengers daily. RailYatri is primarily designed for ticketing booking tickets and train information.
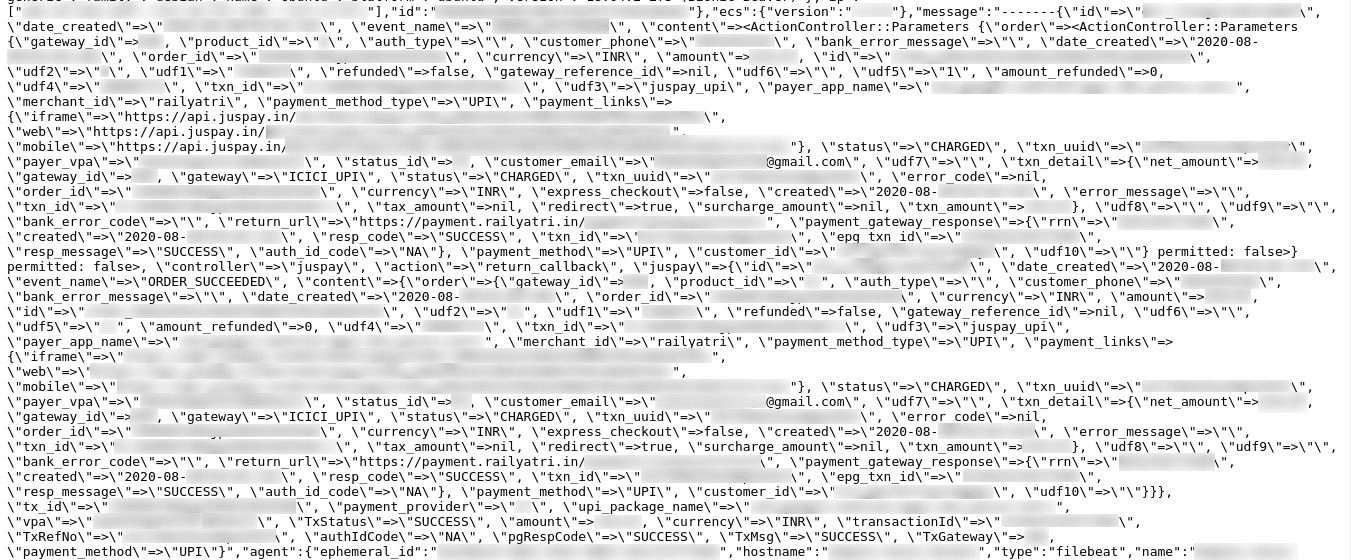
The exposed server was found by a team of researchers led by Anurag Sen at Safety Detectives, a cybersecurity company. Sen and his team found the exposed Easticsearch server on August 10 with 43GB data.
[Read: Why AI and human perception are too complex to be compared]
However, on August 12, a Meow attack cut down most of the data, and the size was reduced to 1GB. For uninitiated, Meow attack is a new type of attack that deletes unsecured databases that run Elasticsearch, Redis, or MongoDB.
The database contained more than 37 million records including log files. The Saftey Detectives team noted that it had more than 700,000 unique email IDs along with other info such as full names, phone numbers, addresses, email IDs, Unified Payment Interface (UPI) ID, and ticket details. Plus, the database had partial information of credit and debit cards, possibly used to booked tickets, and location info of users (through live tracking of trains).
The Safety Detectives team reached out to India’s Computer emergency response team (CERT-In) to highlight the issue on August 17. Later, the server was silently closed without any confirmation from CERT-In or RailTatri.
Despite several attempts to contact RailYatri from Safety Detectives and TNW, there was no response from the portal at the time of writing.
The information stored in RailYatri’s server can reveal a lot about a person, including their address and travel plans. This can be used by attackers or malicious actors to create targeted hacks for these people. Plus, because of the location and travel data, there’s an issue of physical safety as well. Companies like RailYatri that handle sensitive personal data of users should perform regular security audits to avoid exposed servers.
Did you know we have an online event about the future of work coming up? Join the Future of Work track at TNW2020 to hear how successful companies are adapting to a new way of working.
Get the TNW newsletter
Get the most important tech news in your inbox each week.